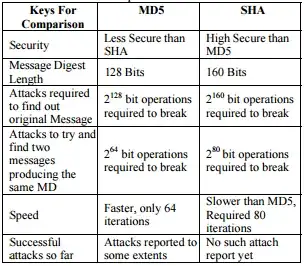
It is well known that SHA1 is recommended more than MD5 for hashing since MD5 is practically broken as lot of collisions have been found. With the birthday attack, it is possible to get a collision in MD5 with 264 complexity and with 280 complexity in SHA1
It is known that there are algorithms that are able to crack both of these in far lesser time than it takes for a birthday attack.
My question is: is MD5 considered insecure only for this reason that it is easy to produce collisions? Because looking at both, producing collisions in SHA1 is not that difficult either. So what makes SHA1 better?
Update 02/2017 - https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html