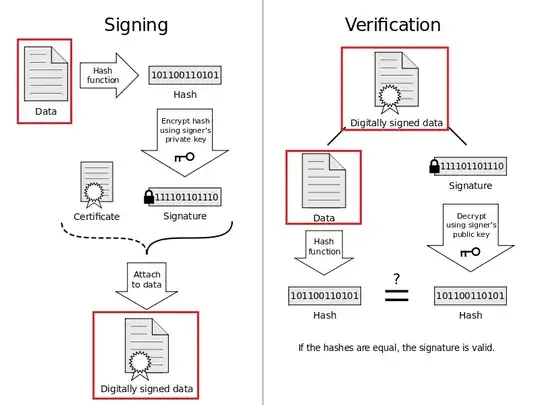
Below is an illustration of the digital signing process.
According to Wikipedia:
A digital signature is an authentication mechanism that enables the creator of the message to attach a code that acts as a signature.
Suppose sender generates private key 1 and public key 1 to generate the signature.
I think sender basically sends the original Data + Certificate (which contains public key 1) + signature to the receiver.
Then the receiver can:
- extract the
public key 1from the certificate - use the public key 1 to decrypt the message hash from the
signature - Use the hash to verify the
original Data.
But what if someone in the middle intercepts the message? He can do all the same as the receiver. Thus the original Data will be exposed. How is this prevented? Is it prevented by using another pair of keys to encrypt the original Data? If so, how is the public key given to the receiver without being intercepted?
I think it is dangerous to send the public key along with the message. But even if you don't send the public key along with the message, the man in the middle can still intercept the public key and keep it for later use.
So, how to keep both confidentiality and authenticity in a public channel, and with all communications happening only on that channel?