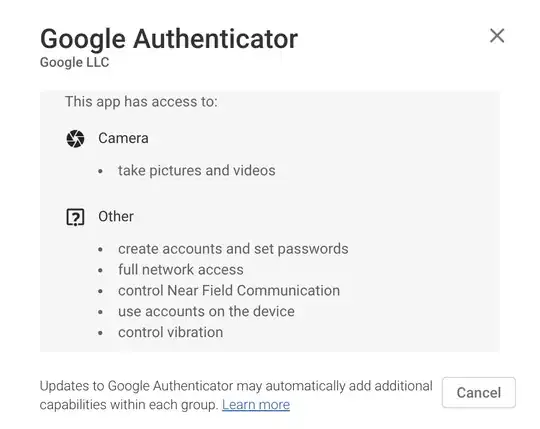
Using a software application like Google Authenticator is a compromise on security made by most users of the Time-based One-Time Password (TOTP) protocol. It is a compromise made for the sake of convenience.
TOTP uses a combination of a secret key, and the time, to generate a code that can be verified by the service you are authenticating with... and which cannot be guessed by someone who does not have the secret key.
There is no network communication required for the One-time Password Generator to operate, except that which may be required initially to fetch a secret key, or synchronize the time. You'll also notice in Google Authenticator that if you have multiple tokens installed, the entire list generates keys constantly while the app is open. So there would be no means of identifying which application you are authenticating with, except to analyze where you leave your focus longest.
Ultimately, you need to be able to trust whatever app is generating your One-time Passwords. If you don't feel you can trust Google, there are other makers of TOTP applications. There are also hardware tokens (presented here as an example... not a brand endorsement). Hardware tokens are much more secure since they are single-purpose and generally tamper-resistant, but have the classic problem of making it difficult to distribute secret keys in the physical space.
In the end, using TOTP is definitely better than knowledge-based authentication - passwords and secret questions - alone, but requires you to have a trusted implementation to generate your passwords from the shared secret and the time. Google Authenticator is the convenient - but not the only choice.