Here's the problem:
Can you trust Tor’s exit nodes?
Excerpt:
Chloe set up a fake website with a Bitcoin theme, downloaded a complete list of exit nodes and then logged in to the honeypot site multiple times via Tor, using a different exit node and a unique password each time.
Crucially the usernames and passwords were sent over regular HTTP rather than encrypted HTTPS so that when Tor’s layers of encryption were peeled back they were visible in the stream of traffic.
If the login attempts had gone unobserved and unabused then the total number of website visits and log in attempts recorded by the honeypot should have matched the number performed by Chloe exactly.
They didn’t.
After a month of testing there were over 600 unexplained page visits, 12 failed log-in attempts and 16 successful ones that hadn’t come from Chloe.
The passwords were not stored anywhere and were far too difficult to guess so if they were indeed stolen, they were stolen by somebody snooping on-the-wire.
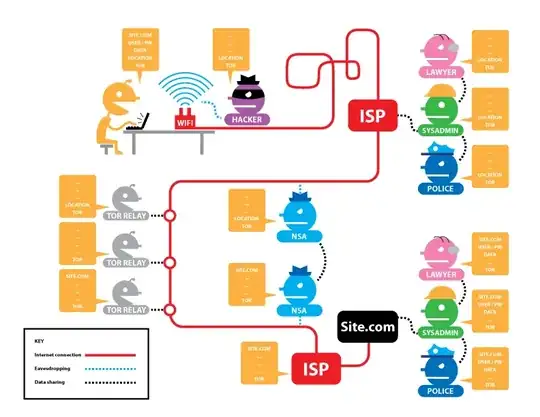
Eventually your network traffic leaves Tor’s safe embrace via an exit node – a gateway computer that decrypts your traffic so it can rejoin the regular internet before it arrives at its final destination.
Anyone can set up an exit node and because it’s the place where traffic is decrypted, anyone who runs an exit node can read the traffic passing through it.
people are using Tor in the mistaken belief that it was an end-to-end encryption tool.
It is many things, but it isn’t that.
MY QUESTION IS: Why not set up the Darknet servers as exit nodes with their web sites at address 127.0.0.1 so there is no "in the clear" traffic over the wire at all?