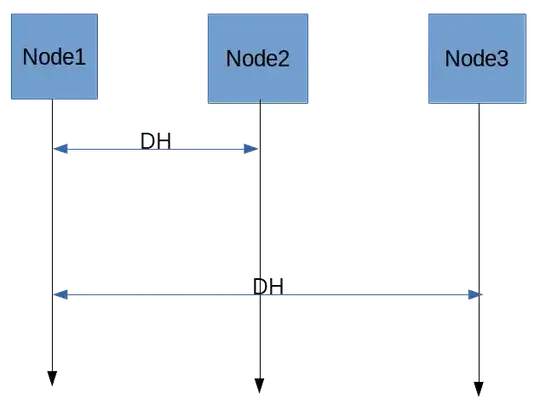
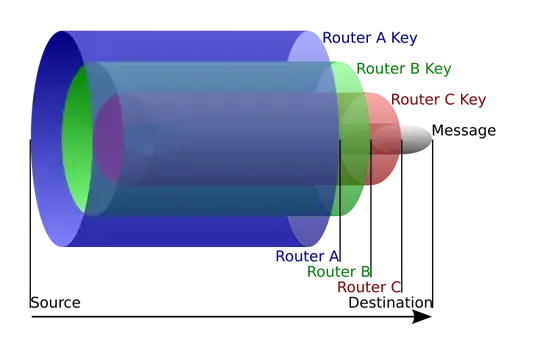
No, the key exchange is done between the client and each relay. This is the general technique behind onion routing. For the modern Tor protocol, the client will exchange a symmetric key (AES128) with three relays using ECDHE (not DHE), specifically using Curve25519. A message being sent from the client will be encrypted three times with each key, and each relay will strip a single layer of encryption. Once the message reaches the exit relay, there is only one layer left, the layer encrypted with the key known by the exit. The exit decrypts it and sends it on its way.
Note that each link between nodes is additionally encrypted using TLS.
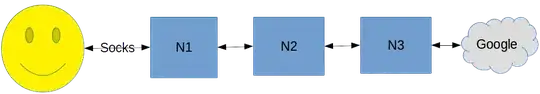
Also note that your diagram is incorrect. The SOCKS protocol is not used to connect to the first relay (the guard), but rather to allow a local program on your computer to connect to your Tor client (usually over localhost). The protocol used to connect to the first relay is the Tor protocol itself.