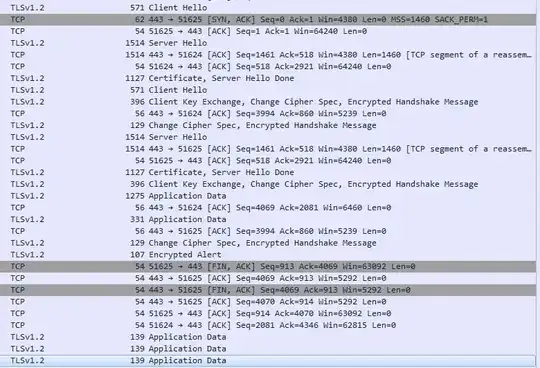
I have the Wireshark capture of a TLS Handshake as shown in the attached image below.
I wish to decrypt the logged traffic that follows. I am a newbie and from what I have read so far, I need a private key to decrypt the data. This key should apparently be accessible from the handshake packets that I have logged. Is that correct?
I only have access to the public key from the Certificate which I guess plays a role to start understanding the handshake capture.
Can someone point me towards information about how I can go about retrieving the private key? Is there another way to gain access to the private key?
As an alternative, I tried logging the SSL keys using the variable SSLKEYLOGFILE but the communication does not seem to be happening directly with the browser, instead via some Java applet embedded in the browser. Even if I can get the applet to dump the keys, I should be on my way. However, I have no idea about how to go about it.
Another alternative would be to manually add the client random (easily found) and the master/pre master secrets (no idea how to find these) to the key log file. Any tips about finding one of these two values will also be very helpful.
I would be grateful for any answers.