Yes, it is possible for previews to execute malicious code. Previews are created by checking the file type, and generating a thumbnail. For images, it resizes them. For videos, it decodes them, seeks into them, and creates a snapshot. For HTML files, it renders them with something like WebKit, and saves a snapshot. While previewers do not intentionally execute code, if any of these complex decoders have vulnerabilities, they can potentially be exploited.
This is a big problem with gstreamer, where a vulnerability in the NSF decoder lead to arbitrary code execution. A similar issue was found in its FLIC decoder. The issues stemmed from the fact that the decoder to use was chosen based on the file contents, rather than the file extension. Because of this, a file with the .mp3 extension could actually contain an NSF file. NSF is the NES audio format, and it is implemented as 6502 bytecode (yes, bytecode). NSF files are played by running it in an actual emulator and converting the output into playable audio. Unfortunately, emulators are complex, and that allowed an exploit entirely in 6502 bytecode to compromise an Ubuntu installation.
While gstreamer is a special case, the fundamental issue where a previewer is able to parse a wide variety of formats simply by navigating to a directory is a nasty security issue. Previews/thumbnails should be disabled if you are concerned about this threat.
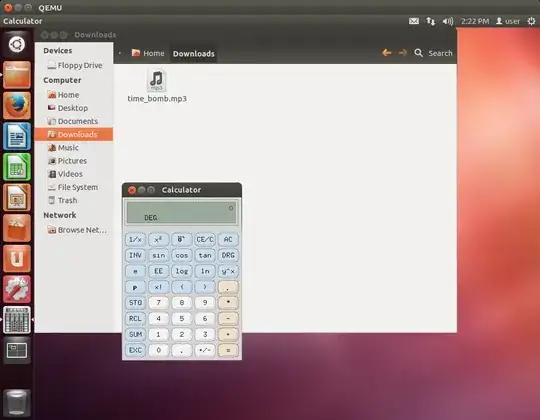
A NSF file, named time_bomb.mp3, exploiting previews on an Ubuntu system to open xcalc: