On my phone I had around 90 verification codes from various companies. 62 of these were 6 digits long. Here's the count of each digit:
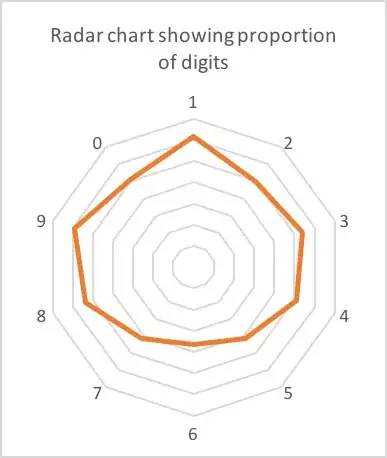
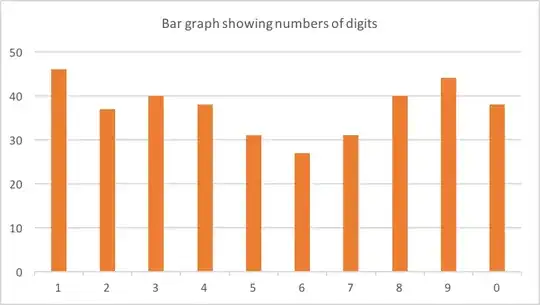
Possibly a slight skew towards 1,8 and 9? Almost certainly just noise in the data (62 is a small sample).
What about double digits?
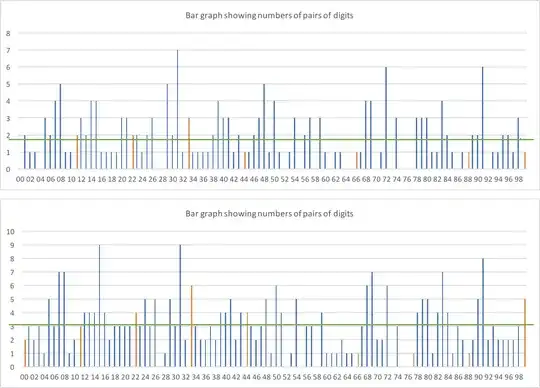 The first graph is only the double digits on the 2-digit boundaries (i.e. AABBCC) - so we'd expect each pair to appear around 1.86 times across the 186 possible digit placements. The second is any placement (i.e. XXX99X counts as a double digit). We'd expect each pair around 3.1 times across the 310 placements.
The first graph is only the double digits on the 2-digit boundaries (i.e. AABBCC) - so we'd expect each pair to appear around 1.86 times across the 186 possible digit placements. The second is any placement (i.e. XXX99X counts as a double digit). We'd expect each pair around 3.1 times across the 310 placements.
There doesn't seem to be any obvious skew with lots more double digits than non double - double digits are shown in orange. In the latter data, we would expect around 31 double digits, and we get 27. That seems reasonable.
Of course, this doesn't rule out other "non random" patterns - but to be honest humans are likely to be searching for patterns - look at these numbers, all taken from my 2FA app: 365 595, 111 216, 566 272, 468 694, 191 574, 833 043.


