Why when we sign up on sites like Facebook and Gmail do our passwords have to be 8-12 characters in length, or some other cap? 8-12 spaces are finite, but you can make your passwords more "secure" by adding uppercase letters and numbers.
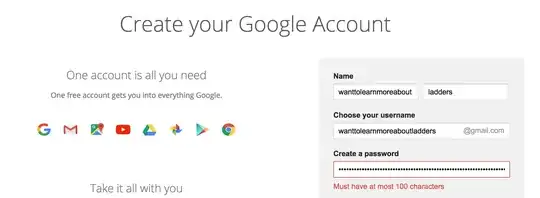
It looks like Gmail passwords cap out at 100 characters (as of Sept 14 2017):
I think that the real reason our passwords are capped in length is for matters of legality, above any shortcomings in cryptographic efficiency. If the company needs to access your account they will access your account and don't want any obstacles in doing so. At first I thought they put a cap on passwords because if they store passwords with longer lengths on their servers they will run out of space on their drives, but char values like passwords doesn't occupy much space, it is just a bunch of letters and numbers after all. Perhaps PBKDF2 with HMAC can decipher passwords of any length, but it will increase CPU processing time in doing so as well as space on a drive (perhaps around 1GB for a very long password).
Should companies with very large data centres be able to accommodate the simultaneous hashing of all the users of their platforms?
Passwords are capped at 12 (or whatever that number may be, 100 for Gmail because Google has the money to accommodate hashing to 100 characters with ease on their systems) because password key derivation function techniques are currently not at a level to decipher passwords of longer lengths efficiently. This means if you wanted to make your password 250 characters long you wouldn't be allowed to because the company doesn't feel it would be equipped to crack your password should they ever have the need to in an efficient manner.
Are we truly free? what motivation do we have to make our passwords more secure than "password" or "12345678" if there is a cap imposed on our security? It seems the message they are delivering is that you can be secure, but not so secure that it makes our job more difficult.
A lock will keep out most intruders, but the ones equipped to crack the lock will do so. Do we choose the lock that will keep the most intruders out, or buy any average lock and hope the ones that can crack it don't come by our houses?
By making our passwords more secure through the addition of uppercase letters and numbers we begin to limit the number of people who can crack the password but people will still crack the password if they want to.