Is it possible for the ISP or any middle point?
If you meant is it possible for the ISP/middle point to decipher/decode/snoop on your chat, then the answer is yes. For unencrypted voice transports, all you need is a wireshark plugin to reconstruct the chat out of the pcap files. Check out http://www.panoramisk.com/151/analyzing-voip-with-wireshark/en/
Comparing with http, is there something like https for voice chat to avoid any possible spying in the middle?
You can run your voice chat over SSL/TLS, that will mean that your data will be encrypted. However you won't be able to leverage the authentication part of TLS as unlike a Server-Client communication in websites, chat softwares are peer-to-peer. To leverage authentication part of SSL, you'll need client certificates which will enable authentication of the other party. If you don't have client certificate, then you never know if you are talking to the right person (a MITM can spoof to be the other party).
Installing client certificates may be possible in an smaller (corporate) setup but may be difficult to achieve on internet where you can basically talk to any client.
Is it practical to encrypt voice data?
Its very practical to encrypt voice data. Many systems do it. Encryption-decryption overhead is no longer prohibitive to decide against it.
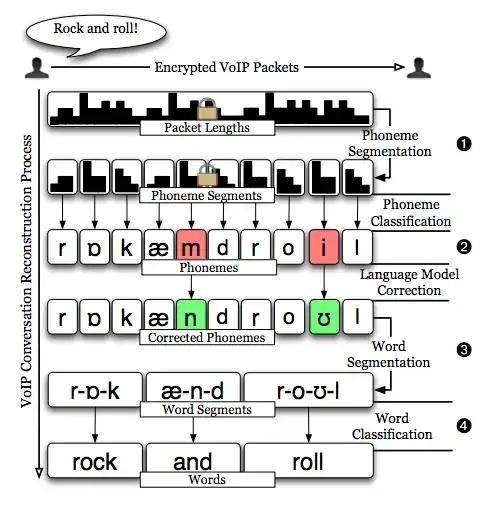 .
.