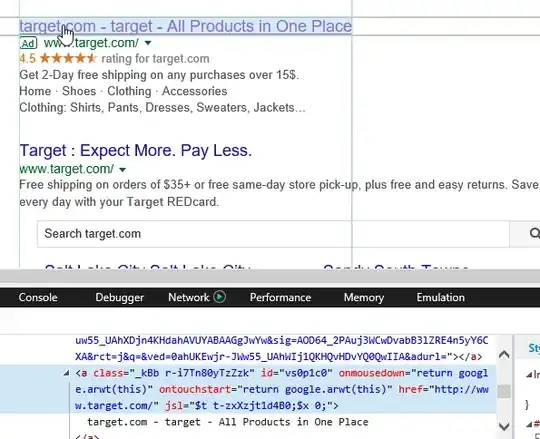
If displaying the wrong URL in the tooltip requires Javascript, how did tech-supportcenter get their Javascript onto the Google search results page?
The scammers did not manage to inject JS into the search results. That would be a cross-site scripting attack with much different security implications than misleading advertisement.
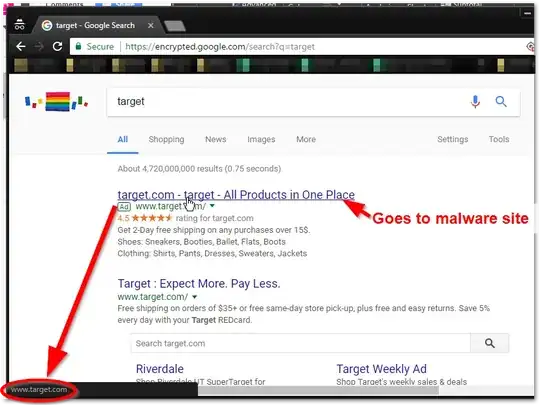
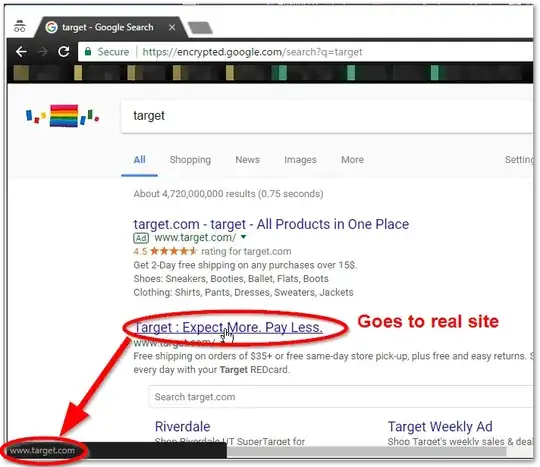
Rather, the displayed target URL of a Google ad is not reliable and may conceal the actual destination as well as a chain of cross-domain redirects. The scammers possibly compromised a third-party advertiser and hijacked their redirects to lead you to the scam site.
Masking link targets is a deliberate feature of Google AdWords. It is generally possible to specify a custom display URL for an ad link which can be different from the effective final URL. The idea is to enable redirects through trackers and proxy domains while keeping short and descriptive links. Hovering over an ad will only reveal the display URL in the status bar, not the real destination.
Here is an example:
- I'm searching for "shoes".
- The first ad link displays
www.zappos.com/Shoes:
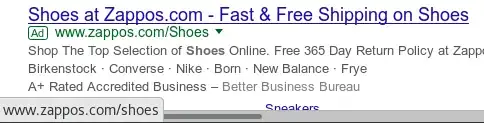
Obviously, Google has strict destination requirements for ad links in place and an ordinary customer won't get their ad approved if they set the link target to a completely different domain. But scammers do occasionally find ways around the vetting process.
At least, Google's policy about "destination mismatches" is pretty clear:
The following is not allowed:
Trusted third-party advertisers may be permitted to issue cross-domain redirects, though. Some of the exceptions are listed here, e.g.:
An example of an allowed redirect is a company, such as an AdWords
Authorized Reseller, using proxy pages. [...]
For example:
- Original website: example.com
- Proxy website: example.proxydomain.com
We allow the company to use "example.proxydomain.com" as the final
URL, but retain "example.com" as the display URL.
One major weak spot is that Google doesn't control the third-party redirectors (in above example, that's pixel.everesttech.net). After Google has vetted and approved their ads, they could simply start redirecting to a different domain without immediately getting noticed by Google. It's possible that, in your case, attackers managed to compromise one of these third-party services and pointed their redirects to the scam site.
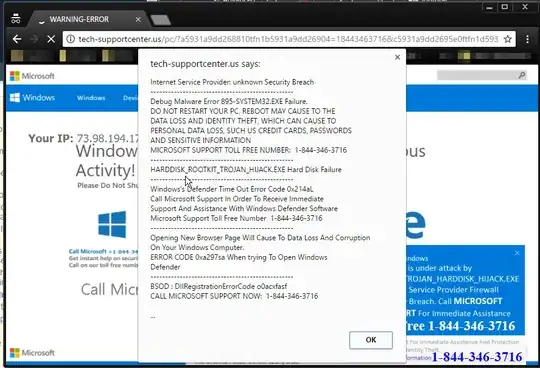
In recent months, there have been several press reports about an almost identical scam pattern, e.g. this report about a fraudulent Amazon ad whose display URL spells out amazon.com but redirects to a similar tech support scam.
(By now, your discovery has also been picked up by a few news sites, including BleepingComputer.)