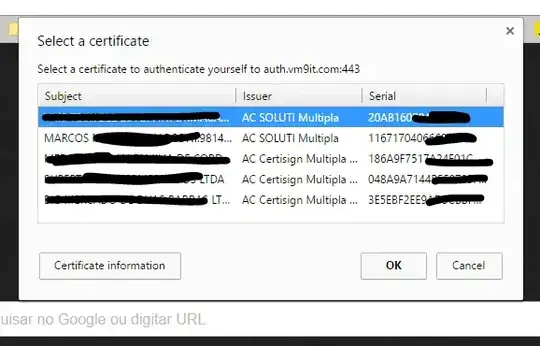
I understand the SSL handshake flow, but I'm facing a logic problem with an abbreviated SSL handshake.
Use case: The user is authenticated on system for common ways, such as passwords. But for some actions the user can be requested to present a digital certificate to confirm your identity. That's has legal implications for some countries like Brazil (ref. http://www.iti.gov.br/icp-brasil), use digital certificate is necessary to confirm that this person (or company) is in fact the person holding that national identity number.
After selecting the client certificate using SSL handshake is necessary to validate it against application to know that its reliable and match with any system user using something like National identification number, that could be on Common Name or another Certificate field (eg. https://pt.wikipedia.org/wiki/E-CPF for Brazilian example).
But, if some reason, the user selects a wrong certificate. It's a valid certificate but, don't match with the user, an error message is sent but I must allow another certificate selection process (ssl handshake) for this user. Some user could have more than one certificate on your PC.
In this scenario, to select another certificate, the user must close the browser and open again, but it gives a negative user experience and I want to improve it.
The solution is very clear, I need to perform a full handshake for every request, so It allows user to select another one.
But how to do that?
The most relevant e question that I found was Avoiding SSL handshake for each call It's exactly opposite of I want to do.
These two definitions are crucial to the general understanding:
- The full handshake is what a client and server do when they don't know each other (they have not talked previously, or that was long ago). In the full handshake, certificates are sent, and asymmetric cryptography (RSA, Diffie-Hellman...) occurs.
- The abbreviated handshake is what a client and server remember each other; moreaccurately, they remember the algorithms and keys that they established in a previous full handshake, and agree to reuse them (technically, they reuse the "master secret" and derive from it fresh encryption keys for this connection).
I posted at my web-server official forum (https://redmine.lighttpd.net/boards/2/topics/7284?r=7286) but their marked my question as invalid **saying that is a client side problem. But is it? ** I can free any information from the browser, close tab, and disable keep alive, but a second handshake doesn't open certificate prompt until I close the browser.
My image bellow is using the Chrome for example and it doesn't have an option "remember my decision", Firefox has. The same happens with Edge, Opera, Edge etc. **Is it a standard? **
I guess, that it can be controlled by server side, requesting a new full SSL Handshake. I made some interventions to try solve it by myself, but was unsuccessful
at client-side:
- Clear all data, even history.
- Open in another sub-domain cookieless
at server-side:
- Send "Connection: close" header
- Disable keep-alive
Close the browser is the only effective for a new SSL Handshake, but it will promote a bad user experience.
It should have a way to renegotiate this authentication.