A lot of services, sites, and applications offer the 'login with Facebook' or 'login with Google' option. For many sites, the browser opens a separate window in which you can enter your username and password. This way, you can check the URL and convince yourself that the origin really is Google/Facebook/whatever. Logging in in this window should be safe, and there is no reason to worry (apart from any privacy concerns you might have).
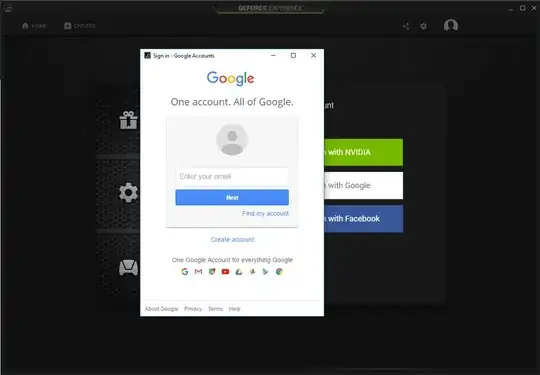
However, this is not always the case. Though I can not find them now, I am quite sure that there are some sites which require you to login with your Facebook/Google account on their site (so the URL shown is not Facebook/Google). I am sure there are some desktop application which do this as well. One example I can give is Nvidia's GeForce experience. Apart from the ridiculousness of having to sign in on Google or Facebook to update a driver, this does not seem to be good practice, since I can't check if I actually login on Google or that the login window is spoofed.
I have read a couple of times that using other services to login is considered good practice. Is this true? I can see some serious problems with it.