I am a computer engineer student. Recently, I was able to arp-spoof the router of my class.
I used:
- Kali
- Ettercap
- Wireshark
- The gateway IP address was: 192.168.0.1
- The victim was my phone with the IP: 192.168.0.34
I was able to see the packets from my phone being sniffed by wireshark on my laptop.
However, I tried using the exact same method on the residential campus network.
- Kali
- Ettercap
- Wireshark
- The gateway IP address was: 192.168.1.254
- The victim was my phone with the IP: 192.168.1.87
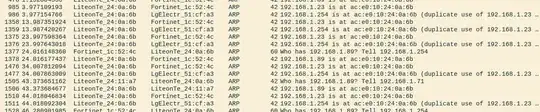
But I doesn't work. The only things that I can sniff on wireshark is the arp packets (Like:
192.168.1.254 is at ec.a5.sd. ...
I think this is because the network is larger and have several layers. But I am not sure, why the arp poisoning is not working on the campus network?