I am a student in computer security and I'm training for a certification.
I have this URL that I want to attack (in a training lab):
http://URL/search/blabla/1
I replaced "1" with letters, as the following:
http://URL/search/blabla/aaa
Which creates this Error Message (I removed some parts to make it clearer):
Fatal error: .... in query — SELECT * FROM Books WHERE 1 AND (LOWER(title) LIKE '%blabla%' OR LOWER(blurb) LIKE '%blabla%') AND (publish_date IS NULL OR publish_date <= '2016-08-23') ORDER BY date DESC LIMIT -5,5'
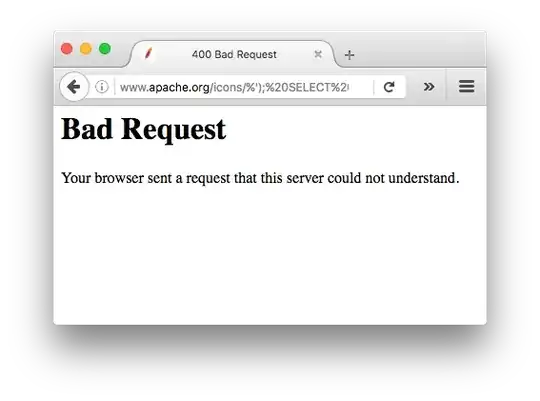
So, first tried to get out of the quote with %'), add a new request and cancel with #:
%'); SELECT * FROM Books;#
=>Bad Request, Your browser sent a request that this server could not understand.
Second try, this time I copy the rest of the request given in the error message and cancel it with a #:
%') AND (publish_date IS NULL OR publish_date <= '2016-08-23') ORDER BY date DESC LIMIT -5,5'#
=> Bad Request again !
Do you think a SQL injection is possible here?