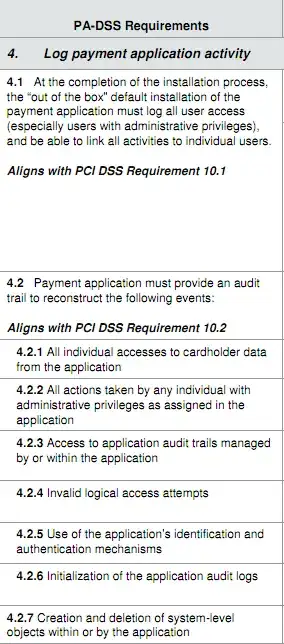
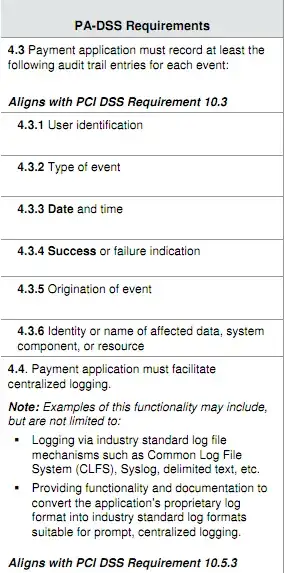
You are expected to log:
- All individual accesses to cardholder data
- All actions taken by any individual with root or administrative privileges
- Access to all audit trails
- Invalid logical access attempts
- Use of identification and authentication mechanisms
- Initialization of the audit logs
- Creation and deletion of system-level objects
These must be logged with a verifiable date & time (proper time sync enabled) in an immutable manner. You should, "Retain audit trail history for at least one year, with a minimum of three months immediately available for analysis (for example, online, archived, or restorable from back-up)."
You'll want to look at the whole document and understand all the sub-requirements that make up the big 12. https://www.pcisecuritystandards.org/documents/pci_dss_v2.pdf
To answer the Jeff Atwood theory, though, and maintain your own sanity, you should keep PCI DSS related logs separate from application activity logs. I would suggest that exceptions be copied into a separate log facility so that from a developer standpoint, logs are readable and sparse. From an auditor standpoint, your comprehensive logs can be, well, comprehensive and used to reconstruct activity.