Link to zxcvbn password entropy demo.
According to zxcvbn, your initial password's stats:
Normal: PwdThing
Guesses:
100 / hour: 5 months (throttled online attack)
10 / second: 58 minutes (unthrottled online attack)
10k / second: 35 seconds (offline attack, slow hash, many cores)
10B / second: less than a second (offline attack, fast hash, many cores)
Doubled: PwdThingPwdThing
guess times:
100 / hour: 9 months (throttled online attack)
10 / second: 2 hours (unthrottled online attack)
10k / second: 1 minute (offline attack, slow hash, many cores)
10B / second: less than a second (offline attack, fast hash, many cores
Letter Doubled: PPwwddTThhiinngg
guess times:
100 / hour: centuries (throttled online attack)
10 / second: centuries (unthrottled online attack)
10k / second: centuries (offline attack, slow hash, many cores)
10B / second: 12 days (offline attack, fast hash, many cores)
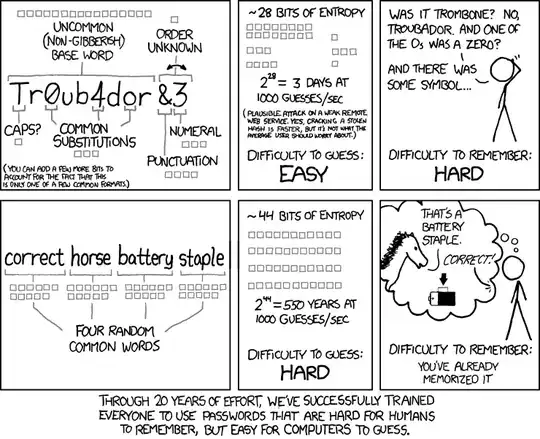
zxcvbn might not be perfect, but I feel like it gives you a pretty good ballpark estimate of your password strength. Play around with it to get a nice memorable password with a high rating.
I prefer sentences to use as passwords. They're long, and inherently difficult to guess and easy to remember.
EX: "My 2nd favorite fruit, on Mondays, is mango!" (spaces included where allowed)
If you're worried about the NSA brute forcing your password... I'd go with the generated passwords everyone else is talking about.