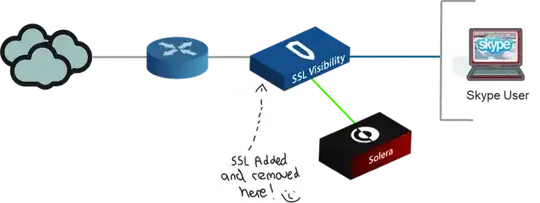
I'm preparing a presentation on Skype networking. And I'd like to demo decryption.
I found a good approach to decrypting the TLS packets captured with WireShark in this blog post:
- Rob Andrews, BlueCoat.com, 2014-01-02, Exploring encrypted Skype conversations, in clear-text (Archived here.)
And I'd like to replicate the general setup scheme on Linux but without using the proprietary tools from the original setup shown here:
I've looked around and found that ssldump could be a suitable tool but some of the tutorials on it are quite complicated. Moreover, they use ssldump independently and without WireShark.
Background:
- Just to clarify, this is for research purposes so you can assume that we have all the certificates or permissions that might be required.
My question is:
- Has anybody reproduced this scheme with free tools?
- If so, what would be the main steps to follow?